Silicon Valley is one of my favorite American TV shows. It tells the story of Richard, a gifted programmer, who accidentally invented a super powerful data compression algorithm. So he set up a company with other partners in the incubator, thus launching a series of ups and downs of entrepreneurial events. The show is full of a large number of computer science elements, so that people in the relevant fields love this series extremely, and the show is also full of many business elements related to entrepreneurship, which makes people feast their eyes. As a graduate student majoring in information security and a silicon valley fan who regards information security as the future career, I wrote this article to summarize almost all the information security elements in the show, and made GIF animations of the corresponding plots to help you review. In addition, there are related knowledge tips that explain professional vocabulary terms. I hope you all like this article.
Season 1 Episode 2
- When Pied Piper was just founded, in order to write a business plan and get investment, Richard and Jared talked to each team member and learned about their job functions and personal skills. As the information security architect and system engineer of the team, Gilfoyle introduced his excellent network security skills.
- Gavin Belson, the boss of the Hooli company, saw that Richard, a former engineer in his company had invented such a strong compression algorithm, hoping to win the business opportunity. So a team of engineers was convened to plan to use reverse engineering to crack Richard’s lossless compression algorithm.
Tip:
Reverse Engineering: reverse analysis and Research on a target product, so as to deduce and obtain the design elements of the product, such as processing flow, organizational structure, functional performance specifications, etc. Its main purpose is to deduce the design principle of the product directly from the analysis of the finished product under the condition that the necessary production information cannot be obtained easily.
Reverse engineering requires engineers to be familiar with the underlying language and program operation logic to reverse analyze compiled software, and then use high-level language to reproduce, which is a very difficult field of information security.
Season 1 Episode 6
- There are no members of pied piper’s team who are familiar with cloud computing. They need a foreign aid, so they plan to hire a young hacker, Carver, to help them build the cloud architecture. Carver boasted that he had hacked into Bank of America system. But in fact, Carver used to work for Bank of America, and then he broke down the bank system. The bank told him not to talk to the public, so he said that he hacked into the system. However, Richard mistakenly thought Carver was highly skilled, so he asked him to help him with other work and gave him access to the database. As a result, Carver broke down pied piper’s system, and Richard fixed it all night.
Season 2 Episode 7
- Pied Piper’s algorithm was partially stolen by Endframe, and now the two companies are competitors. By chance, Gilfoyle got the system login rights of Endframe. He hacked into Endframe’s system and got their trade secrets.
Tip:
Social engineering refers to the way in which people are psychologically affected to make certain actions or disclose confidential information. This is generally considered to be cheating others to collect information, cheat and invade computer systems. This behavior is generally regarded as a violation of privacy. Historically, social engineering is a branch of sociology, but its effect on the psychology of others has attracted the attention of computer security experts.
Season 2 Episode 8
- Because Gilfoyle hacked into Endframe’s system and got their trade secrets. Seth, the security engineer at Endframe, was fired. Furthermore, because of Richard’s strange behaviors, Seth threatened to blackmail Pied Piper. Pied Piper is about to receive a large amount of data from the employer through FTP (File Transfer Protocol), so the system of Pied Piper will be in an extremely vulnerable stage. Richard is very worried about this.
Tip:
Because the early FTP protocol did not do enough security precautions, FTP security is very fragile.
Season 3 Episode 4
- Big head happened to open a business incubator. He took in an entrepreneur who did malware cataloguing.
Tip:
Malware, also known as “rogue software”, generally refers to the spread through the network, portable storage devices and other channels. It deliberately causes the leakage of privacy or confidential data, system damage, data loss and other unexpected failures and information security problems to personal computers, servers, intelligent devices, computer networks, etc., and attempts to prevent users from removing them in various ways, just like “rogue” software. The forms of malware include binary executable files, scripts, active content, etc.
Season 4 Episode 2
- For various reasons, Dinesh took over pied piper and focused on chat platform business. But they inadvertently collected too much data on children, in violation of the COPPA law of the United States. Roughly, they need to pay $21 billion.
Season 4 Episode 3
- Dinesh has a girlfriend Mia, and surprisingly, Mia and Gilfolye belong to the same hacker community. Later in the plot, Mia will be introduced many times as a super hacker. She has done a lot of large-scale illegal hacker attacks. She can be said to be the highest level of hackers in the show. Therefore, Dinesh was very afraid that Mia would retaliate against him after the breakup, so he reported Mia many times to make her in prison.
Season 4 Episode 7
- Gilfoyle was not happy with Jin Yang’s new smart refrigerator, so he hacked it. Gilfoyle privately used the computing power of Pied Piper’s server to crack the back door password of the smart refrigerator.
Tip:
Software backdoor refers to a hacker method that bypasses the security control of software and obtains access to programs or systems from relatively secret channels. In software development, setting backdoor can be used to modify and test the defects in the program. But if the backdoor is known by others, or is not removed before the release of software, then it poses a threat to computer system security.
Season 4 Episode 9
- The Pied Piper team is in urgent need of users to prove the feasibility of their product. They decided to use the phones of the audience at the Hooli fair to download their app. They need a way to hack Hooli’s application and then embed their code. They thought of Mia, Dinesh’s girlfriend in prison. Mia told them they could launch a man in the middle attack with a pineapple router.
Tip:
In the field of cryptography and computer security, man in the middle attack means that the attacker establishes an independent connection with the two ends of the communication and exchanges the data they receive, so that both sides of the communication think that they are directly talking to each other through a private connection, but in fact, the whole session is completely controlled by the attacker.
Wireless pineapple router is a router that allows the user to log in to the attacker’s router. The attacker’s router logs in to the router that the user originally wants to log in, so as to make use of the user’s device.
Season 5 Episode 3
Hooli sent a business spy to work as pied piper’s employee to steal secrets. This spy became Dinesh roommate and intoxicated Dinesh. Finally, he got important information, which is also a kind of social engineering.
Wondering why the secret was leaked, gilfoyle broke through the refrigerator company’s firmware, checked the logs, and found that their products had been listening to users. Although this is not the reason for the leakage of secrets, they also used the discovery to threaten each other, making themselves not subject to legal sanctions.
Season 5 Episode 7
- Gilfoyle advocated the release of cryptocurrency and made slides to Richard. Finally, Pied Piper also chose ICO (initial token issue).
Tip:
Cryptocurrency is a kind of medium that uses cryptography to ensure the security of transactions and control the creation of trading units. As the usual paper money needs anti-counterfeiting design, the anti-counterfeiting of cryptocurrency is a new type of token which is made up of digital currency and virtual currency using cryptography and digital hash and bound with smart contract. Bitcoin became the first decentralized cryptocurrency in 2009, after which the term cryptocurrency mostly refers to such designs.
An Initial Coin Offering (ICO) is the cryptocurrency industry’s equivalent to an Initial Public Offering (IPO). ICOs act as a way to raise funds, where a company looking to raise money to create a new coin, app, or service launches an ICO. Interested investors can buy into the offering and receive a new cryptocurrency token issued by the company. This token may have some utility in using the product or service the company is offering, or it may just represent a stake in the company or project.(from Investopedia)
Season 5 Episode 8
- Competitor companies launched 51% attacks on pied piper’s decentralized network.
Tip:
Decentralized network can prevent any centralized individual from regulating the network by any means for its own purposes. However, when a single unit or organization can control most of the resources, that is, more than 51%, they can monopolize the network.
Season 6 Episode 6
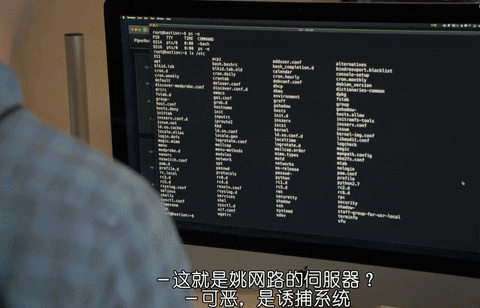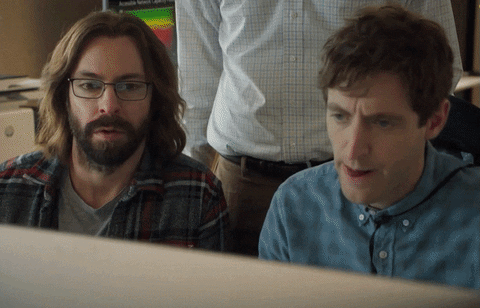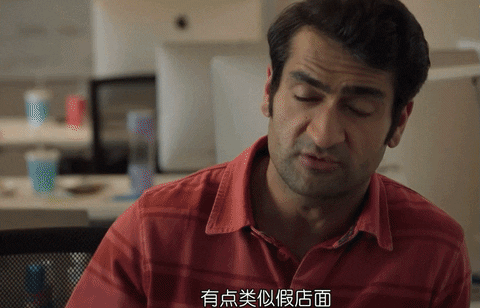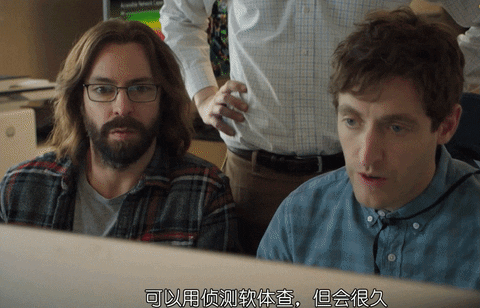
Pied Piper had a network problem and the team suspected it was an attack by the competitor. They asked Jin Yang if there was a back door of the competitor’s software, which could help them log in to the competitor’s system and shut down it.
After logging into the back door, they found out that the software of their competitor, YaoNet, had a honeypot system.
Tip:
Honeypot technology is essentially a kind of technology to deceive the attacker. By arranging some hosts, network services or information as bait, the attacker can be lured to attack them. Thus, the attack behavior can be captured and analyzed, the tools and methods used by the attacker can be understood, and the intention and motivation of the attack can be inferred, so that the defense party can clearly understand what they are facing. Then, the company could use technology and management means to enhance the security protection ability of the actual system.
Season 6 Episode 7
Pied Piper’s program was able to bypass encryption and tamper with Richard’s message, which made them uneasy.
In order to prove the harmfulness of their program, Gilfoyle let their program crack Dinesh’s Tesla password, even though Tesla used the most secure encryption method at the time.
After Pied Piper failed, Gilfoyle and Dinesh founded the Bay Area’s largest cyber security company.
After Pied Piper failed, it seems that Monica went to work for NSA. NSA is the national security agency of the United States. It is the Intelligence Department of the U.S. government agency. It is specially responsible for collecting and analyzing foreign and domestic communication data. It belongs to the U.S. Department of defense, so Monica can’t disclose the company she works for. But from her habit of smoking when she was nervous, the reporter’s guess about her work in NSA was probably right.